The instance profile aws-elasticbeanstalk-ec2-role associated with the environment does not exist.
When working with AWS Elastic Beanstalk, one of the common errors developers encounter is “the instance profile aws-elasticbeanstalk-ec2-role associated with the environment does not exist.” This issue typically arises when there’s a problem with the permissions or configurations related to EC2 instances in your Elastic Beanstalk environment. Understanding why this error occurs and how to fix it is essential to maintain a smooth deployment pipeline in AWS.
Understanding the Problem
The instance profile aws-elasticbeanstalk-ec2-role plays a crucial role in Elastic Beanstalk by defining the permissions needed for EC2 instances to interact with other AWS services. If this profile is missing, improperly configured, or deleted, Elastic Beanstalk environments will not be able to launch EC2 instances, causing the application to fail.
How the error manifests:
- Your environment fails to create or launch new EC2 instances.
- Elastic Beanstalk environment health turns red or stays in a pending state indefinitely.
- Error logs and event notifications in the Elastic Beanstalk console will show “the instance profile aws-elasticbeanstalk-ec2-role associated with the environment does not exist.”
Possible Causes
Several factors can contribute to this issue:
- Deleted Instance Profile: If the aws-elasticbeanstalk-ec2-role instance profile was manually deleted or altered, the environment will not find the required permissions, leading to failure.
- IAM Role Misconfiguration: The instance profile might exist, but its IAM role may lack the necessary policies or permissions to interact with essential AWS resources like S3, CloudWatch, or Auto Scaling.
- Region-Specific Configuration: If you are deploying in a different AWS region, the necessary instance profile might not be automatically created by Elastic Beanstalk.
- Corrupted Environment Setup: Sometimes, the configuration for the environment can get corrupted or incorrectly modified, causing a disconnect between the EC2 instances and their required roles.
Real-World Example
On AWS discussion forums, users have shared their experiences regarding this error. For instance, a developer trying to deploy a Node.js application in Elastic Beanstalk reported that their environment repeatedly failed with the “the instance profile aws-elasticbeanstalk-ec2-role associated with the environment does not exist” error. Upon investigating, they discovered that someone had mistakenly deleted the IAM role associated with the profile. This example highlights how easy it is for such configuration issues to happen, especially in larger teams managing multiple AWS accounts.
Step-by-Step Guide to Resolving the Issue
Now that we’ve covered the causes, let’s walk through how to troubleshoot and resolve the issue.
1. Check the Instance Profile
Begin by verifying that the aws-elasticbeanstalk-ec2-role instance profile exists in your AWS account:
- Go to the AWS Management Console.
- Navigate to the IAM (Identity and Access Management) dashboard.
- Under “Roles,” search for aws-elasticbeanstalk-ec2-role.
- If the role does not exist, you will need to recreate it.
- If the role exists, but the issue persists, ensure it has the necessary permissions.
2. Recreate the Instance Profile (if missing)
If the aws-elasticbeanstalk-ec2-role is missing, follow these steps to recreate it:
- Go to the Elastic Beanstalk documentation for your specific platform (e.g., Node.js, Python, etc.) and follow the guidelines to create a new aws-elasticbeanstalk-ec2-role role.
- Create a new role by navigating to IAM → Roles → Create Role.
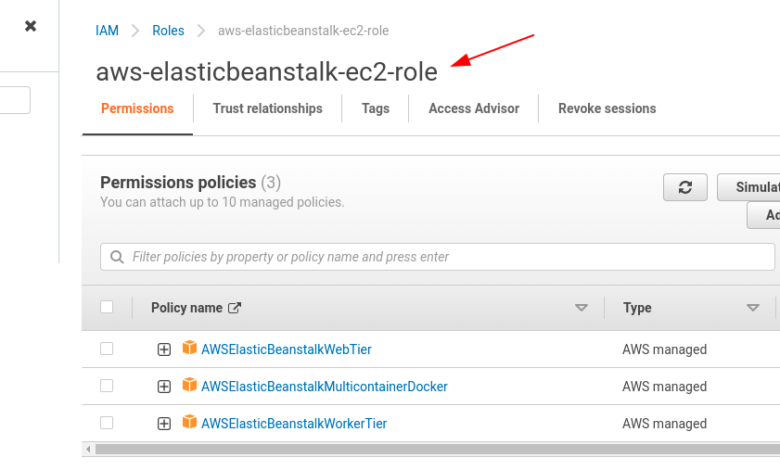
- Choose EC2 as the trusted entity, and attach the appropriate AWS-managed policies like
AWSElasticBeanstalkWebTier,AWSElasticBeanstalkWorkerTier, andAmazonEC2FullAccess. - Name the role aws-elasticbeanstalk-ec2-role and complete the creation process.
3. Update Environment to Use the Correct Instance Profile
After ensuring the instance profile is created or restored:
- Go to the Elastic Beanstalk console.
- Select the environment that is showing the error.
- In the environment settings, update the EC2 instance configuration to point to the newly created or updated aws-elasticbeanstalk-ec2-role.
4. Check IAM Role Permissions
If the instance profile exists but the error persists, verify that the associated IAM role has sufficient permissions:
- Navigate to IAM → Roles.
- Search for aws-elasticbeanstalk-ec2-role.
- Under the role’s permissions, ensure that it has the necessary policies attached (e.g.,
AWSElasticBeanstalkWebTier,AWSElasticBeanstalkMulticontainerDocker,AmazonEC2FullAccess, etc.).
If any policies are missing, add them and redeploy your environment.
5. Rebuild the Environment
If the above steps do not resolve the issue, it might be necessary to rebuild the Elastic Beanstalk environment:
- Create a new environment in the Elastic Beanstalk console.
- Configure the new environment to use the appropriate instance profile and security settings.
- Deploy your application to this newly created environment.
This process helps clear any underlying configuration issues that might be hard to track down manually.
Preventing Future Issues
Once you’ve resolved the “the instance profile aws-elasticbeanstalk-ec2-role associated with the environment does not exist” error, taking steps to prevent it from happening again is essential:
- Avoid Manual Deletions: Ensure that instance profiles and roles are not manually deleted or altered without proper oversight. You can use AWS IAM policies to restrict who can modify instance profiles.
- Monitor IAM Roles: Regularly review IAM roles associated with Elastic Beanstalk and other services to ensure they have the correct permissions and policies. AWS offers tools like IAM Access Analyzer to help monitor and analyze permissions across your account.
- Back Up Configurations: When creating complex environments in AWS, ensure that you maintain a version-controlled backup of your configurations. This will help quickly restore missing components, like instance profiles, in case of accidental deletions.
- Use AWS Config Rules: AWS Config can monitor changes in your environment and trigger alerts if specific configurations, like IAM roles, are modified or deleted. Setting up these rules can give you early warnings before errors affect your deployment.
Conclusion
Encountering “the instance profile aws-elasticbeanstalk-ec2-role associated with the environment does not exist” can be frustrating, especially during deployment. However, by understanding the root causes, such as missing or improperly configured instance profiles, and following the steps outlined in this guide, you can resolve the issue quickly and efficiently. Remember to monitor your IAM roles and prevent manual misconfigurations to avoid future headaches.